
Adversaries targeting the Oil and Gas infrastructures have understood that the OT (operational technology) systems can be targeted due to core challenges such as IT-OT convergence and obsolescence. One of the core reasons many security professionals and OT asset owners do not take the topic seriously is awareness and understanding to the core aspects of the Supply Chain Security process. So, before we start to think about the controls to put in place and/or to develop a strategy, we should be well aware of the supply chain elements, risks, vulnerabilities and assessment approach.
Recently, there was a big security issue with the SolorWinds Orion platform. Attackers put harmful code into the product, affecting over 30,000 organizations. Now, everyone is focused on fixing the Supply Chain process and discussing ways to improve security. But do we really know what supply chain risks are, how they can impact us, and where to start with risk assessment? This blog aims to raise awareness, offer guidance, and help you manage supply chain risks in a methodical way.
What is Supply Chain
Supply chain is a process comprising of resources and process beginning at the raw materials being ingested to manufacturing plants and ending at the consumer level. Supply chain can be very complex and due to every increasing IT-OT convergence the process has become far complex and dense. Everything from the food we consume, our medicines, transportation systems, and our access to the internet rely on a supply chain.
The National Institute of Standards and Technology (NIST) defines Cyber Supply Chain Risk Management (C-SCRM) as the process of identifying, assessing, and mitigating the risks associated with the distributed and interconnected nature of information technology and operational technology (IT/OT) product and service supply chains. It covers the entire life cycle of a system (including design, development, distribution, deployment, acquisition, maintenance, and destruction) as supply chain threats and vulnerabilities may intentionally or unintentionally compromise an IT/OT product or service at any stage.
With respect to Oil industry below is the supply chain process life cycle starting from exploration of the oil to distribution. Each element poses different risks and needs to be managed individually to achieve granular

Cyber Security Risks in OT Supply Chain
Oil and gas infrastructures are known to be resilient and versatile. In the past oil and gas manufacturers we able to quickly respond to cyber security events and other disruptions. This has been most possibly because of redundant pipelines through which operators were able to redirect flow of products. However, it is unsure whether those controls would be sufficient to prevent a large scale cyber nation-state sponsored cyber attack because cyber criminals have become way more advanced and have developed sophisticated attack tactics.
Vulnerabilities within the supply chain process may be purposely or inadvertently introduced, such as through the modification or alteration of hardware/software components, or as a result of poor coding practices, which can potentially be exploited by adversaries. Effectively addressing supply chain risks necessitates the involvement of a multidisciplinary team, encompassing end users, acquisition and procurement personnel, legal advisors, and technical subject matter experts. Let’s delve into the phases of the supply chain process during which vulnerabilities can be introduced.
OT Vulnerabilities introduced during design are mostly unintentional and can affect users of the IACS components. Malicious adversaries can introduce vulnerabilities into IACS components during design of the component that may be installed in organisations worldwide.
During development and production phase vulnerabilities are often accidental and if not identified during testing phase can be costly to fix. During the manufacturing and assembly malicious components can be introduced to the product through poor coding practices and/or intentionally adding a backdoor, which are very difficult to detect.
During the distribution phase malicious actions can often go unnoticed also a limited number of components and customers are affected compared to previous stages.
Insider threats can introduce vulnerabilities and tamper the integrity of equipment during the deployment phase, which will only affect limited number of targets.
IACS equipment under maintenance would already be susceptible to multiple vulnerabilities through a variety of attack vectors such as network access, physical security, exploitation of publicly known vulnerabilities and unpatched systems. Water holing attack is an example of such vulnerabilities introduced into software updates during the maintenance phase, such exploits can have a larger impact.
At last all IACS components should be sanitised before being disposed off, as they may contain plant sensitive Information. Adversaries can attempt to refurbish the components and extract critical information. The refurbished components are also sold at low prices which may contain other organisations data and/or malware.
Supply Chain Gap Assessment
Let’s take a step by step approach to understand how risks around the supply chain security can be assessed, followed by recommendations to work upon. In order to see the real picture we need an assessment strategy, execution steps and an objective to achieve. Like any other cyber security process supply chain can be broken into stages starting from the governance and leading to contingency planning for critical information systems. Below is a step by step approach in a brief and easy to understand format for you to plan your assessment.
Based on the above assessment approach we can easily identify gaps in the design and operational supply chain chain practices. While performing the above actions you can map the existing practices to supply chain elements to identify areas of improvement.
Supply Chain Risk Management (SCRM) and Recommendations
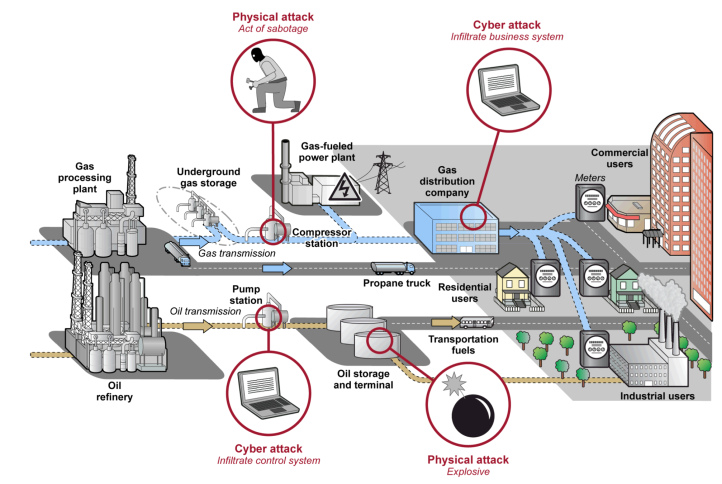
In order to protect your organisation’s digitally connected assets you not only need understanding to your environment but also mapped supply chain elements and risks related to suppliers, vendors, service contractors and customer. Supply chain risks include counterfeit products, insertion of malware, theft, poor coding/manufacturing and development practices. Below is a picture depicting of vulnerabilities in a typical ONG infrastructures.
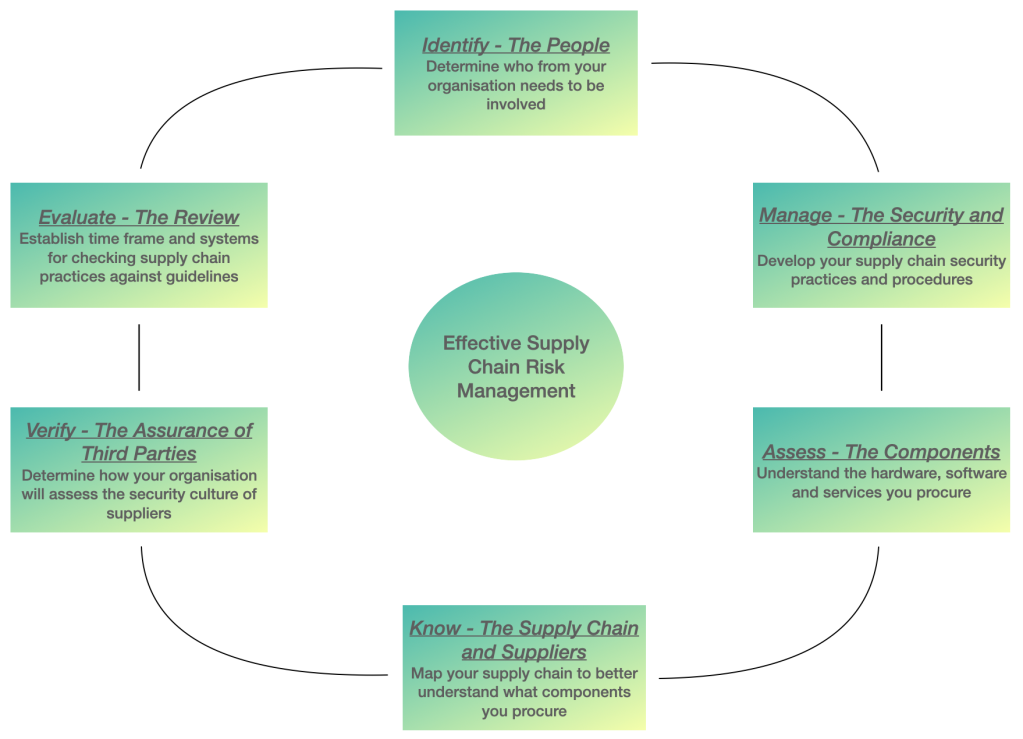
Identify subject matter experts from different teams from various roles and functions (e.g., cyber security, plant automation, governance, physical security, procurement, legal etc.) to form a committee. Ensure all members well-informed, well-aware and well-trained in the security procedures of their role or function.
Design and develop you supply chain policies and procedures that can help you address governance, cyber security, third-party security, compliance management. Take reference from sector and industry best practices such NIST on how to conduct supply chain risk management. Involve senior leadership to to drive top-down culture in your organisation.
Collect all information regarding the IACS components (asset inventory; hardware/software/applications) currently deployed in you environment, which help you enable achievement of business objectives. The ultimate idea is to be aware about what you have and what risk it make impose. Perform detail risk assessments to know what you are exposed to and how it can be controlled.
Know your suppliers and vendors, also get an awareness round the sub-suppliers involved in the supply chain. Due to rise in outsourcing trend it is highly advisable to be aware and understand what risks your suppliers and sub-suppliers can bring in as part of larger ecosystem. Perform analysis such as crown jewel analysis to understand what is critical to enable your business and ensure risks around those components are assessed. Apply the security polices on your suppliers which are applicable internally.
Promote and encourage your suppliers to maintain and adhere to your organisation’s security culture. Develop procedure and process then can help you perform supplier reviews to address supply chain security risks. Establish master security requirements and mandate adherence to it by all suppliers involved. Involve contractual clauses in project agreements and to perform regular reviews to control the risks.
Perform regular review of supply chain risk to ensure your SCRM program is upto date. Perform regular reviews and check the level of compliance against the master security requirements. Gradually you will notice that the controls around supply chain risk are improved continuously.
Conclusion
Vulnerabilities can occur due to human error, it is important that everyone have some working knowledge of C-SCRM and secure by design principles. It takes a multi-disciplinary team to appropriately address cyber supply chain risk. If keen to achieve maturity gradually establish a organisation wide supply chain risk management practices, understand and know your suppliers, define supplier review process, establish master security requirements and ensure supply of critical information system components. Also, changing perspective and providing suppliers with conditional trust will change an organisation’s decision matrix.
Remember three main principles of supply chain risk management outlined by NIST.
- Supply chain risk management is a multidisciplinary effort.
- Building supply chain security is as important as cybersecurity.
- Human error is the most common root cause of a security breach.
References
- NIST 800-161 Cyber Supply Chain Risk Management Practices for Systems and Organisations: https://csrc.nist.gov/publications/detail/sp/800-161/rev-1/draft
- Free Supply Chain Risk Management course: https://fedvte.usalearning.gov/publiccourses/cscrm/index.htm
- Vendor Supply Chain Risk Management (SCRM) Template: https://www.cisa.gov/sites/default/files/publications/ICTSCRMTF_Vendor-SCRM-Template_508.pdf
- CISA Supply Chain Risk Management (SCRM): https://www.cisa.gov/supply-chain
- CISA Supply Chain Risk Management (SCRM) Essentials: https://www.cisa.gov/publication/cisa-scrm-essentials
- American Petroleum Institute Oil and Gas Industry Preparedness Handbook: https://www.api.org/-/media/Files/Policy/Safety/ONG-Industry-Preparedness-Handbook-v2.pdf

Thanks Shivendra
It is in pipeline, stay tuned.