
Defending industrial automation control systems (IACS) environment is now a part of every critical infrastructure’s cyber security operations. Gone are the days when we used to understand and identify threats based on network protocol anomalies. Threat adversaries have been keeping up their pace with the defensive security advancements to evade detection. The attacks are becoming more sophisticated and now demands a structured approach to understand adversary behaviour in order to minimise the risk through threat informed defence.
We all have been in the past were running behind fixing loopholes and implementing controls without understanding the systems behaviour, dependancy and attributes. Constantly our world moved around a monolithic approach to manage the cyber security risks, due to the evolving cyber attack sophistication we need to opt for segmented security. Today our blue teams, incident responders, threat analysts, risk champions have the privilege to understand the threat adversaries better by utilising publicly accessible threat behaviour knowledge bases such as MITRE ATT&CK(1) and go beyond the technical elements such as anomalies and IOCs (indicator of compromise).
What is MITRE ATT&CK ?
MITRE is a not-for-profit organisation, which works in the public interest across United States federal, state and local governments, as well as industry and academia. ATT&CK (Attacker/Adversary Tactics Techniques and Common Knowledge) is a publicly accessible database of threat adversary behaviour based on real-world data. The MITRE ATT&CK framework provides a structured approach to understand how a threat can materialise in your environment and do you have the capability to defend against those TTPs (tactics techniques and procedures).
Tactics: Common goals ICS Cyber attackers
Techniques: Common mention utilised to achieve goals
The ATT&CK framework is divided into groups of tactics mapped to a high level technique to help you breakdown the complex cyber kill chain into granular and manageable pieces such as below.

Basically the threat behaviour data has been taken into account from thousands of real-world OT security incidents published, which are mapped to technique an adversary utilises to cause harm. The objective was to create a knowledge base of attack style and common pattern observed. The network anomalies (protocol based) and IOCs (IPs, hashes, domains, etc.) are those technical elements which helps us foster the base level understanding of any threat. But one thing which stays static (or slowly evolve) is the behaviour/attack style of the threat even if they change their attacking tools.
How you can internalise it ?
The best way to assess your preparedness level against the common threat groups and common attack vector is to test your environment by emulating real-world threats. Testing your capabilities will enhance your understanding with respect to the existing controls whilst identifying the potential gaps to looks into.
To start with you can look at MITRE ATT&CK home page(1) to learn more about the framework followed by the free courses from ATTACKIQ academy(5). Once you have gained the working level knowledge about operating the matrices and ATT&CK navigator you can start to look for threats applicable to your industry. For instance If you want to know the threat groups and adversaries you are exposed to just search in the MITRE ATT&CK homepage (check below screenshot of reference) click in the search bar and type the industry type.


From the above listed results we can see the threat groups commonly observed in each industry type. Clicking on the threat group will take you to a page which provides you a brief description of the threat group, list of techniques they utilise and software/tools they utilise (check below screenshot for reference).
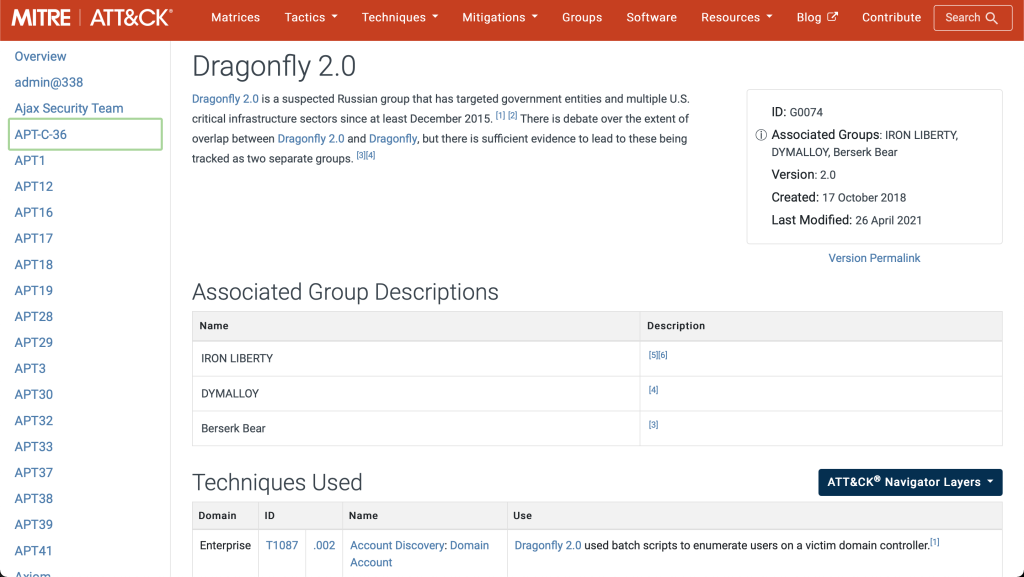
Moving on you can create a map of techniques DRAGONFLY threat group uses to attack their targets (click on the “ATT&CK Navigator Layer” button shown in previous screenshot and choose view). Note: The below view is a representation of the enterprise ATT&CK Navigator.

Now you know the techniques you need to focus on and assess your environment against these. While assessing your environment an effective way would be to base your cyber threat scenarios and test cases around these techniques to emulate real-world threats, preparing adequate defence measures and achieve a credible risk rating.
Next we can start to look in to specific details about the above highlighted techniques. In order to do so browse to https://collaborate.mitre.org > choose tactics > initial access > drive-by-compromise. In the below screenshot you can see the dragonfly group your industry is exposed to and the list of possible mitigations. Clicking further on the each mitigation will provide you with more useful information (I will leave that to you).
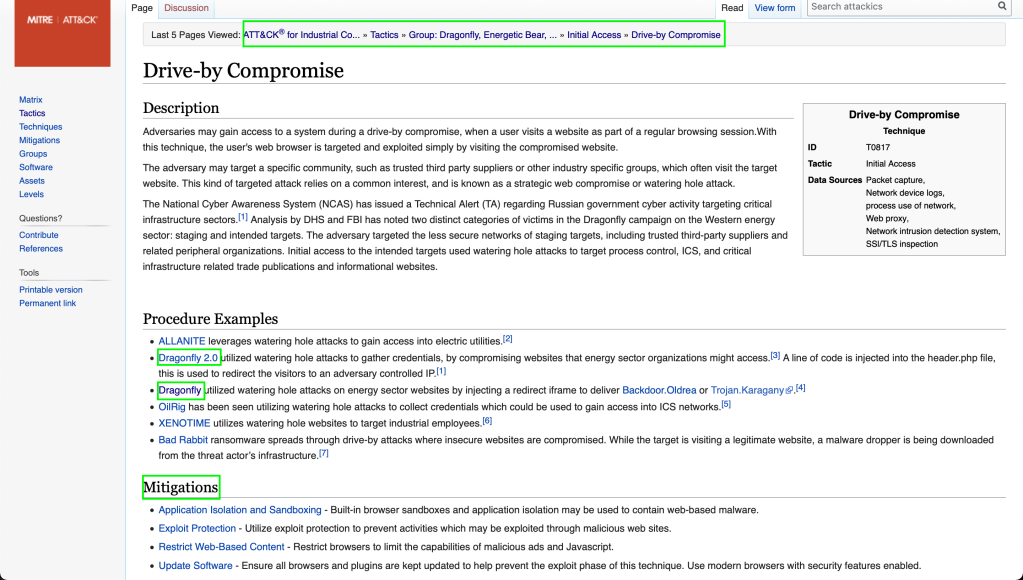
The above mentioned approach is an easy way to keep track of threat groups individually you are susceptible to and managing your cyber attack surface. Also, the above demonstrated method can be utilized while modelling cyber threats during risk assessments, table tops exercises, threat adversary emulations.
To track multiple threat groups you can opt to procure a sophisticated and automated tool such as one developed by ATTCKIQ(6), DRAGOS, Nozomi or you can manually use excel sheets to run down tests. The automated tool gives you the liberty of choosing the assets (from inventory) and run specific techniques against each of them to identify the gaps. The automated tool would provide your facility to run specific targeted tests such as WannaCry ransomware, TRITON, STUXNET, etc.
Manually Using ATT&CK Navigator for Mapping Threats
Let’s use the same threat group and dissect it into specific granular details of tactics and techniques through ATT&CK navigator and an excel based tracker (source:ATTCKIQ). You can follow along the below mentioned steps to re-produce the same.
Step1: Open Attack Navigator(7) and choose ICS.


The above listed matrix is a representation of commonly observed ICS tactics and techniques an adversary utilises during an attack. The complete cyber kill chain has been broken into manageable elements for granular threat/attack surface management.
Step 2: Now click on “multi-select” option to choose “Dragonfly” from the threat groups listed.
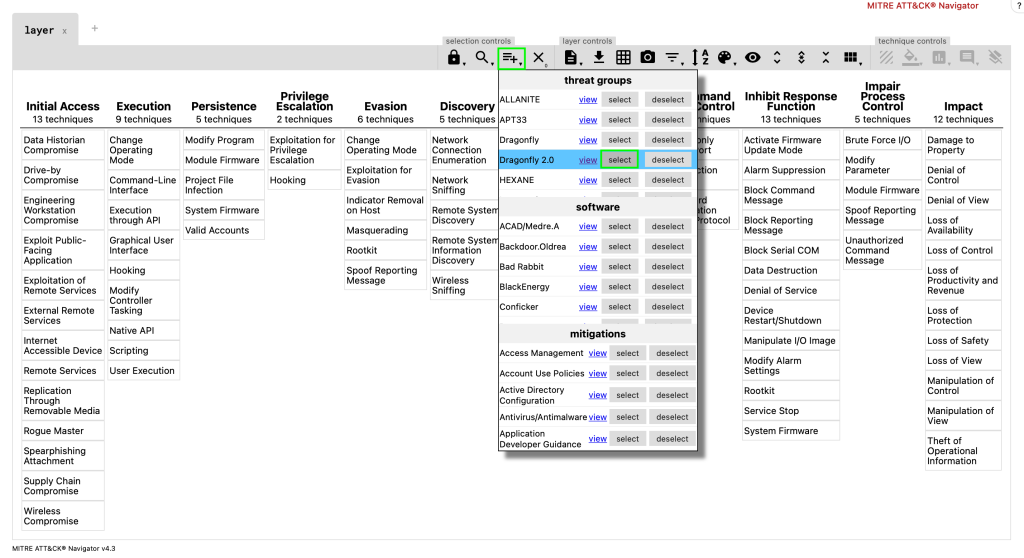
Step 3: One selected click on the colour utility to highlight selected cells.

Step4: Now use an excel tracker of your choice to list down the tactics and techniques applicable to create a 2X2 matrix. Red and Blue teams can help further to list down the source of technique and defensive measures your organisation has along with the expected and actual result. Look at the below table for reference I have created for Dragonfly (based on assumed controls).

The above table can be used as part of table-top exercises, purple team emulation, adversary emulation, risk assessments, security assessment, incident response drills, etc. The objective here to focus on a threat group applicable to your environment, assess your defensive capabilities and fix the gaps.
Conclusion
The above listed methodology definitely looks simple, however the key here is to remember the purpose behind creation of ATT&CK, which is to capture and understand threat adversary behaviour so do not rush it. Do your homework before you jump into playing around with the ATT&CK navigator. For those like me who have been struggling in the past to structure their approach this is for you. I am certain that the ATT&CK framework is going to evolve year after year so do keep an eye here, starting from the security analysts to C-suite executives everyone can utilise the framework to support their day-to-day operations and decision making. For the long run it is critical that we shift from detecting anomalies to threat behaviour analysis and create a more sustainable and defendable environment to practice threat informed defence.
Alex Stamos, former chief security officer of Facebook, called ATT&CK “an extremely useful resource for companies trying to explore all of the areas they should be considering.
Source: mitre.org
Resources
- MITRE Blog: https://medium.com/mitre-attack
- Protecting Critical Infrastructures: https://www.mitre.org/publications/project-stories/protecting-critical-infrastructure-from-cyber-threats
- DRAGOS: https://hub.dragos.com/hubfs/Whitepaper-Downloads/Mapping-Industrial-Cybersecurity-Threats-to-MITRE-ATTACK-for-ICS.pdf
- Nozomi: https://www.nozominetworks.com/blog/your-guide-to-the-mitre-attack-framework-for-ics/
- ATTACKIQ Academy: https://academy.attackiq.com/
- ATTACKIQ: https://attackiq.com
- ATT&CK Navigator: https://mitre-attack.github.io/attack-navigator/